The global coronavirus pandemic has forced a new reality where millions of people across the world now work from home. And although a majority of the discussion is—rightly—focused on social distancing, flattening the curve, developing treatments, and coping with quarantines and self-isolation, a largely overlooked aspect has been the threat of COVID-19 on the cybersphere.
The large-scale transition to work-from-home (WFH) opens the door to two main cybersecurity threats. One, individuals and companies become more vulnerable in these times, and two, a higher rate of attacks also means a higher probability of success. Although WFH has some interesting and significant benefits, employees usually don’t have the same tools and mechanisms in place at home to protect their work and their privacy.
Noam Froimovici, general manager of Kaspersky Israel, tells NoCamels that the transition to WFH is riskier to organizations than they realize. “There’s no deep thought or deep consideration for the field of information security or the security of this transition. And this process itself actually makes this whole field more dangerous,” he explains.
First, employees working on their own devices from home may immediately expose their organizations to potential threats lurking in their personal devices. This is because we use our personal devices differently than our work devices.
On our personal devices, there are no limits to what websites we visit, files we download, and content we upload. On the work devices, there is usually a set list of programs we use and tasks we carry out, and because our behavior is largely predictable, our organization knows what measures are required to protect our device from viruses and attacks. In addition, on company devices, employers may install software that monitors employee activity to ensure the proper use of company resources. Company devices also often have anti-virus software installed to protect the integrity of the device from any viruses an employee may download by mistake.
“Incidents that in the regular work environment would raise a red flag, now are likely to slip under the radar” because irregularities are being attributed to the changes in work format, Froimovici tells NoCamels.
Another threat is that employees who are not used to using their personal computers for work are prone to make mistakes that may expose their personal data to their company’s network. For example, accidentally uploading or sending the wrong file from a work computer means that you still sent work-related media, while the same mistake on a home device may result in sending sensitive personal information.
Those who usually take their work devices home aren’t free from risk either. Although company devices usually have mechanisms to protect the device and the information on it, employees’ personal internet network is likely not as protected. Most companies have firewalls in place and monitor network traffic for suspicious activity that may compromise their systems.
Major organizations, such as tax authorities and the Israel National Insurance Institute (Bituach Leumi), may be most at risk. “Infrastructures are now a lot more open, those state services are now a lot more vulnerable, government workers are now accessing government networks from personal computers just to keep services up, but it makes government systems completely vulnerable,” Froimovici explains.
Generally speaking “even just from a statistical standpoint, the number of endpoints, or entry points, of an organization, is growing like the coronavirus itself—exponentially,” he says.
As criminals and hackers are aware of the economic pressure the world is under, “we estimate that we will see more and more attempts to penetrate systems that are now opened, but that a month ago were not. The effect of this will be catastrophic, and this is where we’ll need to cope with a much larger number of incidents,” he warns.
Zoom-bombing and phishing
As WFH has become the norm, communication via video platforms has also risen exponentially, and these have become popular targets. Zoom, for example, has added more videoconferencing users so far in 2020 than all of 2019, and attacks where uninvited guests access a session by exploiting privacy settings—known as “Zoom-bombing”—have increased as well. Trolls and threat actors use the session to attack guests and display inappropriate or shocking imagery.
Israeli cybersecurity giant Check Point has noted a marked increase in suspicious registration on Zoom.
“During the past few weeks, we have witnessed a major increase in new domain registrations with names including ‘Zoom.’ Since the beginning of the year, more than 1,700 new domains were registered and 25% of them were registered in the past week. Out of these registered domains, 4% have been found to contain suspicious characteristics,” the company’s research arm wrote in a post on Monday.
But Zoom is not the only application targeted by cyber criminals. “New phishing websites have been spotted for every leading communication application, including the official classroom.google.com website, which was impersonated by googloclassroom\.com and googieclassroom\.com,” according to the research.
The pan-European policing agency Europol recently warned that phishing attacks are also on the rise. In a report titled “Pandemic Profiteering: How Criminals Exploit the COVID-19 Crisis,” Europol said “criminals have used the COVID-19 crisis to carry out social engineering attacks, namely phishing emails through spam campaigns and more targeted attempts such as business email compromise (BEC).”
These criminals, the agency warned, “are abusing the demand people have for information and supplies.”
“There is a long list of cyberattacks against organizations and individuals, including phishing campaigns that distribute malware via malicious links and attachments, and execute malware and ransomware attacks that aim to profit from the global health concern,” said the report, published on March 27.
Researchers at Israeli-founded global endpoint protection company Cybereason have observed hundreds of phishing attacks that use COVID-19-themed files and domains to spread malware all over the world. People are eager to get new information about the spread of the virus and new health guidelines and are therefore a lot more vulnerable to phishing attacks disguised as this sought-out information.
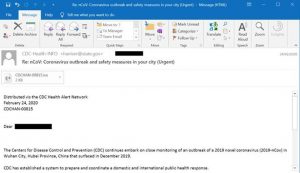
According to a recent report by Cybereason titled “Just because you’re home, doesn’t mean you’re safe,” cyber adversaries are sending emails with malicious files and publishing apps that all seem to be developed and sent by legitimate sources such as the World Health Organization (WHO). Consequences of these attacks have gone as far as shutting down a hospital which has one of the biggest COVID-19 testing facilities in the Czech Republic.
Such attacks “are particularly threatening and carry very real risks to human lives,” Europol noted in its report.
Cybereason also shared some tips on how to lead a more security-aware WFH environment. These include first checking the authenticity of the sender and assessing if the email address and content make sense, being wary of shortened links, and pay extra attention to emails that ask for confidential or sensitive information such as credit card or bank information, home address, and passwords. Legitimate organizations would not ask for this sensitive information to be sent over email, the company points out.
The dark web and COVID-19
The pandemic has also had a significant impact on dark web operations and activities.
Dov Lerner, a security researcher with Israeli cyber intelligence company Sixgill which focuses on deep web and dark web analyses, tells NoCamels that the discourse on the pandemic in dark web communities focuses on several aspects, including profiteering and conspiracy theories.
“In any natural disaster, we see the scammers, the people who are looking to profit, and they play to people’s fears. But this is unprecedented at scale,” he says. “There are people selling masks for USD 20 apiece [given the shortage in medical gear], touting ‘miracle’ cures, and setting up charity and aid schemes to profit from donations.”
The Europol report noted that vendors on the dark web are selling illicit goods at higher prices as source materials become unavailable and are offering “special corona goods (scam material) at discounts.”
Lerner says there’s also a noted uptick in the development of ransomware attacks such as those on healthcare providers “because there’s a lot of money to be made out of people’s fears—and their hopes.”
Since the dark web is a community of communities, there are also rampant conspiracy theories about the origins of the novel coronavirus and other details and, in some forums, there is even radicalization. “The dark web is a feeding ground for conspiracy theories and if members radicalize one another, this could lead to real-life violent actions,” he tells NoCamels. An example he provides is of a forum member threatening to gun down people he’s encountered allegedly not observing social distancing directives.
“The dark web is an extension of the real world and there are all sorts of people in those forums,” Lerner says.
COVID-19 international anti-hackers league
Amid the threats, a new group of cyber experts from over 40 countries formed this month to protect frontline medical resources and critical infrastructure.
“We are a community of CTI (cyber threat intelligence) experts, incident responders, and industry experts working to neutralize all cyber threats looking to exploit the current pandemic,” the group, called the COVID-19 CTI League, says on its site.
“Our goal is to foster a positive community, dedicated to sharing information and protecting end-users from COVID-19 cybersecurity threats (and have a little fun in the process),” it said.
The league was founded by Ohad Zaidenberg, a lead cyber intelligence researcher at the UK-based company Clearsky and a former course commander in the elite IDF Unit 8200 (according to his LinkedIn profile); Nate Warfield, a senior security program manager at Microsoft; Chris Mills, a senior privacy program manager at Microsoft; and Marc Rogers, VP of cybersecurity strategy at Okta.
The group now has over 600 members, Zaidenberg indicated this week on Twitter.
“If anyone is sick enough to use this global crisis to conduct cyberattacks, we need to try to stop them,” he told Israel Defense.
This article first appeared in NoCamels, which covers innovations from Israel for a global audience.



